Where to start
The first thing on the list for the smart static is to get an internet connection with enough bandwidth to hopefully be able to stream Netflix, Prime, etc. As well as enough for any smart switches, bulbs, the odd camera, etc.
I’ll cover the multimedia and smart devices in other posts, but needless to say, I have come up with non-internet solutions too just in case.
Using coverage maps I worked out the best provider. I will be starting with “3”, speed tests show I should get around 15Mbps which should be enough for most things. I will trial a pay as you go SIM with the possibility of swapping it out if it doesn’t deliver.
I wanted the core of this network to be as simple as possible, i.e. if I could find one device that was, AP, Router, Firewall, VPN client in one device that would be the dream. Off to the internet I went…
There are a few manufacturers that fit the bill; the big ones being MikroTik, Draytek, TP-Link and (a company I’ve never heard of) GL-Inet.
A quick look at all of them and Draytek was going to be more than I wanted to spend (and I’d probably need a USB 4G “modem”). The cheaper TP-Link models didn’t allow external aerials, something that I would like to have the option of at a later date, and I wasn’t 100% sure if they supported OpenVPN.
This left Mikrotik and GL-Inet…
MikroTik
I have used MikroTik products before and am reasonably comfortable configuring and using them. Their catchy named wAP ac LTE kit, ticked all the boxes and was in a price bracket that looked good (around £170), it was also allowed for external setup if needed. I have a MikroTik hAP mini that I used on my FTTC connection at home. This router fell into second place, mostly on cost, but also because I thought I’d like to try another manufacturer and add another string to my bow.

GL-Inet
GL-Inet are a smallish company, they use the open source OpenWRT as the base for their devices and add a nice GUI on top. They have some pretty amazing features because of this, OpenWRT has a package manager which allows you to add lots of addons if you need for various use cases. The device that fitted my brief the best was the GL-AP1300LTE, it seems that all niche LTE devices have insanely unmemorable names!
GL appear to have started life creating a small travel router based on OpenWRT and grown from there.
The GL-AP1300LTE costs just under £140, a saving compared to the MikroTik and a new routing platform to learn if I wanted. Purchased from Amazon this device was the winner… There was plenty of hair pulling I am sure I wouldn’t have had with the MikroTik, but it was a great learning experience too… Ironically it was a post about a MikroTik router that fixed the final VPN issue I had!

The GL-Inet Journey
Fortunately I have two internet connections at home at the moment (FTTC & FTTP), for the rest of this post, the FTTP connection will be the house, which is true. FTTC will be the caravan, which will be switched to LTE longer term.
Within 10 minutes of unboxing the device I had it connected to the internet (via FTTC at home), connected back to the house over VPN (routing only VPN traffic and allowing local internet breakout), and guest wifi. Things were good…
Except I couldn’t route VPN traffic from the house to the caravan, I spent a few hours trying to work out why, thankfully I had a RealVNC license spare so I could access the caravan pi (more on that later) over the internet. I hit a brick wall, it should have worked… I came back to it a few times and never got it working. I enlisted the help of internet strangers, friends, any one who would listen..
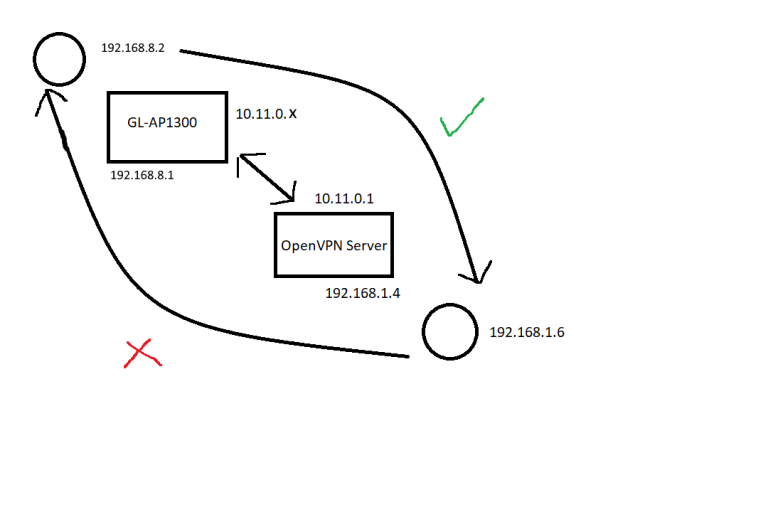
With 3/4 of the VPN working, I decided to leave it, occasionally working at bits, waiting for the next GL firmware release.
Then randomly I decided I would try and replicate the setup on my hAP mini to see if I could make it work with a MikroTik, after all I could change my mind and return the GL. I found an excellent article on how to get the MikroTik to talk to pfSense OpenVPN server. There was one paragraph in there that I hadn’t seen on any of the previous posts “Add Client Specific Overrides for Mikrotik subnets”, so I figure I would check I could get the MikroTik to work, within minutes I had VPN traffic flowing.
I plugged the GL back in, added the client specific override for that VPN on OPNSense and woohoo, all the traffic.
The lesson here is that despite the fact I was using different hardware and different firewalls, sometimes the answer is out there, in the weirdest places!
Edit: Add details about client specific overrides:
Add Client Specific Overrides for Mikrotik subnets.
Although all the local/remote subnets have been added to the pfSense OpenVPN server configuration, it doesn’t know which clients have which remote subnets and will drop the incoming traffic because it’s not in the OpenVPN routing table for that OpenVPN client.
A client specific override is added to the pfSense OpenVPN configuration, this is matched based on the certificate name the client is using, it’s best practice to use unique names/certificates for each client during implementation which identify the site/client clearly.
Because the OpenVPN client should be connected you can use the pfSense OpenVPN status page to copy and paste the exact certificate name of the connected OpenVPN client. Important settings are as follows:
- Common Name is set to the client certificate name.
- iroute <network> <netmask> for each remote network of that client is added in the Advanced field.
The OpenVPN server is restarted to force the OpenVPN client to reconnect and apply the changes, the network routes will now appear in the OpenVPN routing table in the status page.